File Info
| Exam | Palo Alto Networks Certified Network Security Administrator |
| Number | PCNSA |
| File Name | Palo Alto Networks.PCNSA.VCEplus.2024-08-28.203q.tqb |
| Size | 9 MB |
| Posted | Aug 28, 2024 |
| Download | Palo Alto Networks.PCNSA.VCEplus.2024-08-28.203q.tqb |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
How does an administrator schedule an Applications and Threats dynamic update while delaying installation of the update for a certain amount of time?
- Disable automatic updates during weekdays
- Automatically "download and install" but with the "disable new applications" option used
- Automatically "download only" and then install Applications and Threats later, after the administrator approves the update
- Configure the option for "Threshold"
Correct answer: D
Question 2
You receive notification about new malware that infects hosts through malicious files transferred by FTP.
Which Security profile detects and protects your internal networks from this threat after you update your firewall's threat signature database?
- URL Filtering profile applied to inbound Security policy rules.
- Data Filtering profile applied to outbound Security policy rules.
- Antivirus profile applied to inbound Security policy rules.
- Vulnerability Prote ction profile applied to outbound Security policy rules.
Correct answer: C
Explanation:
Reference:https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/policy/security-profiles Reference:
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/policy/security-profiles
Question 3
URL categories can be used as match criteria on which two policy types? (Choose two.)
- authentication
- decryption
- application override
- NAT
Correct answer: AB
Explanation:
Reference: https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/url-filtering/url-filteringconcepts/url-category-as-policy-match-criteria.html Reference: https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/url-filtering/url-filteringconcepts/url-category-as-policy-match-criteria.html
Question 4
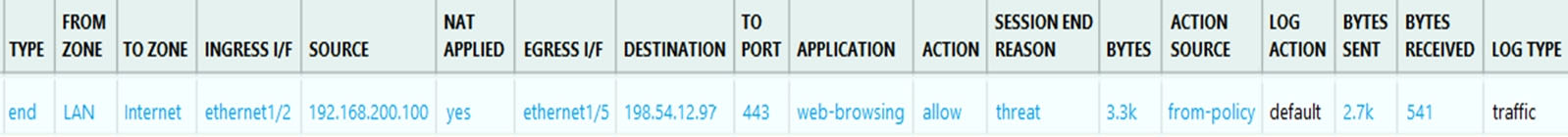
Given the screenshot, what are two correct statements about the logged traffic? (Choose two.)

- The web session was unsuccessfully decrypted.
- The traffic was denied by security profile.
- The traffic was denied by URL filtering.
- The web session was decrypted.
Correct answer: CD
Question 5
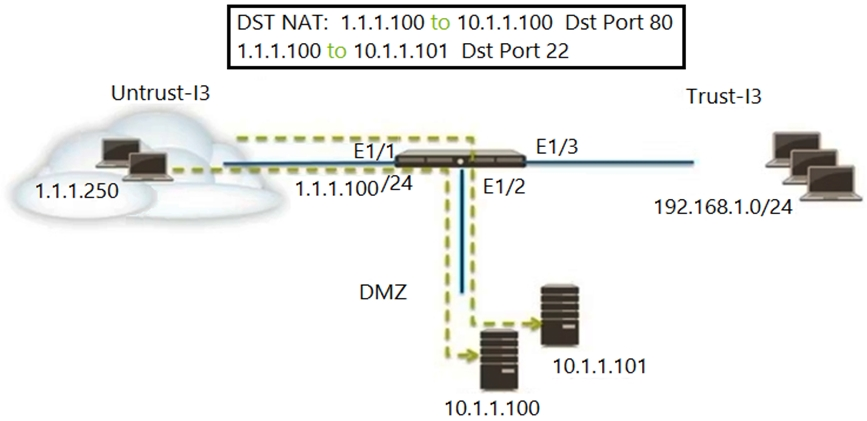
Refer to the exhibit. An administrator is using DNAT to map two servers to a single public IP address.
Traffic will be steered to the specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and Host B (10.1.1.101) receives SSH traffic.

Which two Security policy rules will accomplish this configuration? (Choose two.)
- Untrust (Any) to DMZ (1.1.1.100), ssh - Allow
- Untrust (Any) to Untrust (10.1.1.1), web-browsing -Allow
- Untrust (Any) to Untrust (10.1.1.1), ssh -Allow
- Untrust (Any)to DMZ (10.1.1.100. 10.1.1.101), ssh, web-browsing-Allow
- Untrust (Any) to DMZ (1.1.1.100), web-browsing - Allow
Correct answer: AE
Question 6
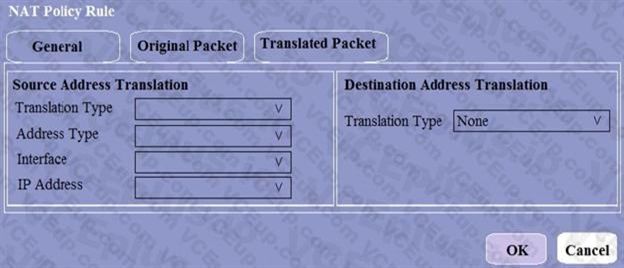
When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?

- Translation Type
- Interface
- Address Type
- IP Address
Correct answer: A
Question 7
Which interface does not require a MAC or IP address?
- Virtual Wire
- Layer3
- Layer2
- Loopback
Correct answer: A
Question 8
A company moved its old port-based firewall to a new Palo Alto Networks NGFW 60 days ago. Which utility should the company use to identify out-of-date or unused rules on the firewall?
- Rule Usage Filter > No App Specified
- Rule Usage Filter >Hit Count > Unused in 30 days
- Rule Usage Filter > Unused Apps
- Rule Usage Filter > Hit Count > Unused in 90 days
Correct answer: D
Question 9
What are two differences between an implicit dependency and an explicit dependency in App-ID?
(Choose two.)
- An implicit dependency does not require the dependent application to be added in the security policy
- An implicit dependency requires the dependent application to be added in the security policy
- An explicit dependency does not require the dependent application to be added in the security policy
- An explicit dependency requires the dependent application to be added in the security policy
Correct answer: AD
Question 10
Recently changes were made to the firewall to optimize the policies and the security team wants to see if those changes are helping.
What is the quickest way to reset the hit counter to zero in all the security policy rules?
- At the CLI enter the command reset rules and press Enter
- Highlight a rule and use the Reset Rule Hit Counter > Selected Rules for each rule
- Reboot the firewall
- Use the Reset Rule Hit Counter > All Rules option
Correct answer: D
Explanation:
References: References:


